am 13.11.2023 - 11:25 Uhr
From an economic perspective, IT security is a relevant foundation for securing the business model of a data center, not least because concrete commitments to availability are typically specified in service-level agreements. However, in the past decades, the structure, layout, and technical equipment of data centers have undergone comprehensive changes.
In this context, the Federal Office for Information Security (BSI) revised the definitions of the terms 'data center' and 'server room,' which originated from the mid-1990s. Recommendations and requirements, such as those in the minimum standards according to § 8 para. 1 BSIG, have been formulated in a more practical manner.
The legal framework For the operation of data centers, a variety of laws and regulations now apply, including:
the Law on the Federal Office for Information Security (BSIG), the IT Security Act (IT-SIG2), the Directive on measures for a high common level of cybersecurity across the Union (NIS2 Directive), and the Critical Entities Resilience Directive (CER) as the KRITIS umbrella law. For example, BSIG § 8a specifies: "Operators of Critical Infrastructures are obliged to take appropriate organizational and technical measures to prevent disruptions to the availability, integrity, authenticity, and confidentiality of their information technology systems, components, or processes."
Disruptions in data centers Disruptions in data centers can occur due to internal and external factors. Internally induced disruptions to availability, integrity, authenticity, and confidentiality affect the fundamental operational safety of the data center infrastructure. The ICONAG specialist article "Checklist for the Use of a Management and Operating Device (MBE) with an Energy Management System (EnMS) in Data Centers" outlines important steps to prevent such disruptions in the planning and implementation of a Management and Operating Device (MBE) within the framework of Datacenter Infrastructure Management (DCIM) (The checklist can be ordered).
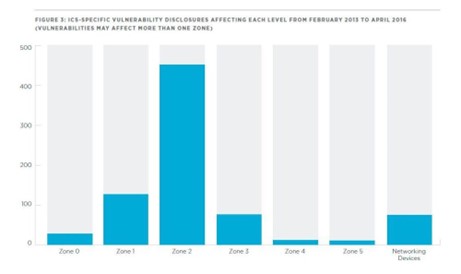
Externally induced disruptions typically involve sabotage, espionage, or unauthorized access. Sabotage involves interference with a system by an external party, leading to disruptions or failures, often with the aim of extortion for ransom. Espionage poses a threat by illicitly accessing information to spy on business internals and secrets. Unauthorized access to the building is intended for theft.
The most important regulations for IT security specifically applicable to building automation are:
It should be noted that there is no 100% IT security for building automation either. The protection requirements for a highly available data center are considered to be high or very high.
Specific precautions to be taken in the field of building automation must be derived from a risk analysis for the respective use case. In the BSI standards and basic protection compendium, the following threat scenarios for building automation are considered particularly significant:
INVITATION TO ONLINE SEMINAR
On Tuesday, November 21, 2023, ICONAG-Leittechnik, B-Unity, and Infrontec Ingenieurgesellschaft will host the online seminar "Monitoring as the Basis for High Availability and Energy Efficiency in Data Centers."
From 1:30 PM to 5:30 PM, the following topics will be covered in various presentations:
Operating data centers within a regulatory framework, ensuring resilience and energy optimization Legally compliant infrastructure monitoring in data centers. What are the requirements of the Building Energy Act and the Energy Efficiency Act? Requirements for building automation in critical infrastructure data centers Key building automation management functions and data interfaces relevant for data center operations The speakers possess expert knowledge and extensive experience in their respective roles, such as managing a data center in a major German city, working at the German Air Traffic Control, and in the planning, consulting, and implementation of infrastructure management for data centers. Participation is free of charge.
Inadequate planning of building automation, for example, due to lack of redundancies or high complexity in the collaboration of different trades.
Faulty integration of building services systems (Technical Building Equipment) into building automation can, for example, lead to a minor fault in one trade restricting the function of the entire building automation.
Use of insecure systems and protocols in building automation, for example, due to lack of updates to building services systems due to age or inadequate maintenance.
Faulty configuration of building automation can lead to IT systems overheating in certain weather conditions or non-functional interaction of building automation systems in crisis situations.
Manipulation of interfaces from standalone building services systems to building automation, resulting in erroneous reactions of the building automation, for example, triggering all doors to open due to a manipulated fire alarm system message.
Furthermore, the BSI identifies the following deficiencies in Technical Building Management (TGM) or Data Center Infrastructure Management (DCIM) as sources of risk:
Lack of basic IT security principles for TGM planning, as operators are often not yet determined during planning.
Insufficient documentation in TGM leads, for example, to uncertainties about the current status of IT security and unclear relationships that cannot be traced in a crisis.
Deliberate or unconscious compromise of interfaces with TGM, especially when sensitive areas are connected to TGM, such as security services, fire alarm systems, automation stations with increased security requirements (Safety Instrumented Systems - SIS).
Inadequate monitoring of building services systems, for example, critical system malfunctions not being detected.
Inadequate role and authorization management, for example, when multiple persons use the same user account or permissions of former users are not revoked.
General risk analysis for a data center
The risks in infrastructure management for data centers (DCIM) are frequently considered in planning and operation through corresponding systems and processes for business operations. An exception may be the consistent monitoring of building services systems, especially in smaller data centers.
It can be assumed that, at the latest by the implementation of the Building Energy Act and Energy Efficiency Act by 2025, improvements will be made, and all data centers will be equipped with management and control systems as well as energy management systems as part of Datacenter Infrastructure Management.
Also, for the field and automation level of building automation, it must be ensured that availability, integrity, authenticity, and confidentiality of data are guaranteed. Most risks arise when automation systems are connected to the internet.
The Derivations
As derivations from practical requirements for building automation for the execution and operation of data centers from the BSI Basic Protection Compendium in conjunction with VDMA 24774 (2023-03) IT Security in Building Automation, the following points may be particularly relevant and serve as a useful guide. It is assumed that in data center operation, an elevated level of IT security is already ensured, and the fundamentals thereof do not need to be explicitly listed again:
Derivations as requirements for the planning of building automation
Encrypted data transmission / communication (KNX-Secure, BACnet SC, OPC/UA,…).
Deactivation of all unnecessary services and access points from the factory ("hardened" devices and software), including documentation of the ports used.
Management software with features for recording user activities (Audit Trail).
Acceptance of the building automation system with the latest firmware (automation stations) or software version (BBE, MBE), at least all security-relevant updates, especially the latest patches from Windows and the latest versions of the software systems used.
Derivations for the implementation or execution of building automation systems
Setting up physically or virtually separate IP networks for building automation, including securing particularly vulnerable network segments with firewalls.
Secure access for remote maintenance.
Establishment of a backup concept for automation stations and management level, including instructions for recovery.
Physical security of control cabinets, technical rooms, for example, including deactivation of USB or Ethernet access.
Malware protection and latest security patches for engineering tools.
Project-specific adjustment of access authorizations and password changes (especially on automation stations, BBE, MBE), activation of auto-logoff functions.
Post-hardening of systems by deactivating or deleting all unused services, physical accesses, user accounts, processes, and programs (especially on automation stations, BBE, MBE), activation of auto-logoff functions.
Creation of work instructions and behavioral instructions for the permanent maintenance of IT security by the installer (SOP = Standard Operating Procedure).
Creation and handover of a building automation network documentation with model designations of the components, MAC addresses, installation location, and firmware versions.
IT security training for operators.
Derivations for the operation of building automation systems
Individual usernames and passwords.
Regular security-relevant updates/upgrades (especially for PCs, servers, and routers), ensuring that updates are only downloaded unaltered from certified sources.
Regular backups of plant programming, configuration, configuration changes of MBE software, and stored operational data.
Ensuring compliance with work instructions and behavioral instructions, including regular updating of the IT security concept as part of the maintenance of the GA system.
Regular IT security training.
Advice
There is no 100% security for availability, integrity, authenticity, and confidentiality of data in building automation. However, by specifying and observing simple technical and organizational measures, a good level of security can be achieved. In summary, the following 5 tips:
Determine the protection requirements for each building based on a risk analysis. This must be done jointly by specialist planners, operators, and clients.
Be aware that building automation systems, classified as Purdue Zone 0 to 3, are particularly vulnerable to IT security, with the greatest risks currently arising from the connection of building automation to the internet.
Based on a security concept, make specific IT security requirements for planning, implementation, and operation based on VDMA 24774 (to be offered as a special service of the GA).
Issue work instructions and behavioral instructions (policies) to prevent and mitigate damage.
Agree on software maintenance and system maintenance to regularly close known security vulnerabilities.
In the course of regular maintenance, not only check compliance with the policies but also the currency of the security concept.
The ICONAG MBE (Management and Operating Device) software has been certified as B-AWS (BACnet Advanced Workstation) according to the latest BACnet Revision 19. |
Powered by ModuleStudio 1.3.2